Anne Borre Events & Insights
Exploring the latest trends and stories from Anne Borre.
Cybersecurity: The Invisible Shield We Can't Ignore
Uncover the secrets of cybersecurity—your invisible shield against digital threats. Don't let your data be the next victim!
Understanding the Basics of Cybersecurity: Why It Matters
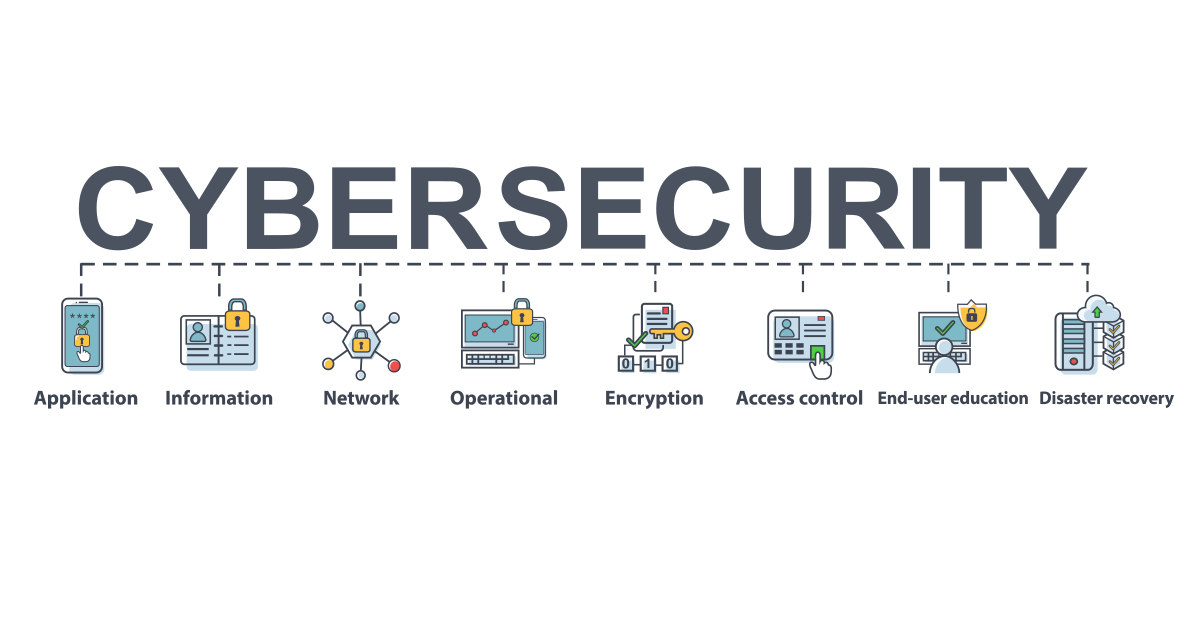
Understanding the basics of cybersecurity is crucial in our increasingly digital world. Cybersecurity refers to the practices and technologies that protect networks, devices, and data from unauthorized access and attacks. As more individuals and organizations rely on technology for everyday tasks, the threats posed by cybercriminals grow more sophisticated. According to the Cybersecurity & Infrastructure Security Agency (CISA), without robust measures in place, sensitive information can be compromised, leading to severe financial and reputational damage.
Cybersecurity matters not only for large enterprises but also for small businesses and individuals. A single data breach can result in significant losses, affecting trust and customer loyalty. According to a report by IBM Security, the average cost of a data breach is over $4 million, highlighting the importance of cybersecurity investment. By understanding the basics of cybersecurity, individuals and companies can implement strategies to safeguard their digital assets effectively, ensuring a safer online environment for everyone.
Top 10 Common Cyber Threats You Need to Know
In today's digital landscape, understanding cyber threats is crucial for both individuals and organizations. This blog post will outline the Top 10 Common Cyber Threats you need to be aware of to keep your information secure. From phishing scams to ransomware attacks, these threats are evolving constantly. According to the Australian Cyber Security Centre, awareness of these common vulnerabilities can significantly reduce the risk of falling victim to cybercriminals.
1. Phishing: Often considered the most common cyber threat, phishing involves tricking users into providing sensitive information.
2. Malware: Malicious software that can damage or disrupt systems.
3. Ransomware: A particularly damaging type of malware that locks data until a ransom is paid.
4. Man-in-the-Middle Attacks: These occur when attackers secretly intercept and relay messages between two parties.
5. Denial of Service (DoS): This attack floods a system, making it unavailable to users.
6. SQL Injection: A code injection technique that allows attackers to interfere with queries to a database.
7. Zero-Day Exploits: Threats that exploit vulnerabilities before the developers have a chance to fix them.
8. Credential Stuffing: Using stolen username and password combinations to gain unauthorized access.
9. Insider Threats: These can be either intentional or unintentional risks posed by employees.
10. IoT Vulnerabilities: As more devices connect to the internet, they present numerous security challenges. For more details on these threats, visit the Cybersecurity & Infrastructure Security Agency.
Is Your Business Safe? Key Cybersecurity Measures to Implement
In today's digital landscape, ensuring that your business is safe from cyber threats is more critical than ever. Implementing robust cybersecurity measures can prevent potential data breaches and safeguard sensitive information. Key strategies include regular security audits, which help identify vulnerabilities, and adopting a cybersecurity framework that aligns with industry standards. Additionally, establishing a comprehensive incident response plan will prepare your team to react promptly and effectively in the face of a cyber attack.
Another essential measure for ensuring business safety is employee training. Educating your staff about the importance of cybersecurity can significantly reduce risks. Regular training sessions should cover topics such as recognizing phishing attempts, the significance of strong passwords, and safe internet browsing practices. Furthermore, implementing multi-factor authentication (MFA) adds an extra layer of protection, making it harder for unauthorized users to gain access to company systems.